Cybersecurity has become a crucial issue for small and medium-sized businesses (SMBs). During the Stratégie PME trade show, Roland Winters, Director of Cybersecurity at Commissionnaires du Québec, presented a conference titled: “Integrating Cybersecurity into Your SMB: What You Absolutely Need to Do.” Through real-world examples and practical recommendations, he provided essential tools to help businesses protect themselves from growing cyber threats. The full video of this conference is available below.
Video: Watch the full conference by Roland Winters, Director of Cybersecurity at Commissionnaires du Québec.
Summary
- Current Threats: The most common cyberattacks in 2024.
- Strategic Approach: Understanding cybersecurity frameworks.
- Risk Assessment: Identifying and prioritizing threats.
- Practical Solutions: Training, technologies, and adapted processes.
- Conclusion: Security in constant evolution.
Current Threats: Understanding the Issues
Small and medium-sized businesses (SMBs) are increasingly exposed to sophisticated cyber threats. During the Stratégie PME trade show, Roland Winters highlighted three major types of attacks in 2024: ransomware, sophisticated phishing, and organized cybercrime.
Ransomware: A Growing Threat
Ransomware is a type of malicious software that encrypts victims’ data, demanding a ransom for its release. In 2024, this threat has reached alarming levels. According to a Sophos survey, 67% of organizations in the energy, oil/gas, and utilities sector were affected by ransomware in 2024, the same rate as in 2023. Additionally, the average cost of recovery after a ransomware attack in this sector stands at $3.12 million.
SMBs are not spared. A study by Hornetsecurity reveals that 55.8% of reported ransomware incidents in 2024 affected small businesses, highlighting their vulnerability. Cybercriminals specifically target these organizations, which often have weaker protections, to maximize their profits.
Sophisticated Phishing: Social Engineering at Work
Phishing remains a preferred method for cybercriminals to deceive individuals and businesses. In Southeast Asia, from January to June 2024, Kaspersky’s anti-phishing technology detected 336,294 phishing attacks targeting various organizations. These fraudulent campaigns exploit human trust, using social engineering techniques to trick victims into disclosing sensitive information or downloading malicious software.
SMBs are particularly vulnerable to these attacks due to a general lack of cybersecurity awareness among employees. Cybercriminals take advantage of this weakness to infiltrate systems and steal valuable data.
Organized Cybercrime: A Lucrative Industry
Organized cybercrime has become a thriving industry, generating billions of dollars by exploiting both human and technological vulnerabilities. Structured criminal groups carry out complex operations, combining various attack techniques to maximize their impact.
For example, online scam centers in Southeast Asia exploit thousands of people to defraud victims worldwide, generating billions of dollars for organized crime. These sophisticated operations demonstrate cybercriminals’ ability to orchestrate large-scale attacks, targeting both individuals and businesses.
The Urgency of a Proactive Cybersecurity Posture
In light of these growing threats, it is crucial for SMBs to adopt a proactive approach to cybersecurity. This includes implementing robust protection measures, continuously training employees, and actively monitoring systems to detect and counter potential attacks.
By strengthening their digital resilience, SMBs can not only protect their assets but also ensure business continuity and maintain the trust of their customers and partners.
Strategic Approach: Choosing the Right Cybersecurity Framework
To counter growing cyber threats, businesses must rely on proven cybersecurity frameworks. These tools provide clear guidelines for identifying, managing, and reducing risks. During his conference, Roland Winters introduced three key frameworks tailored to the needs and resources of various organizations.
CIS Controls: An Accessible Solution for Small Businesses
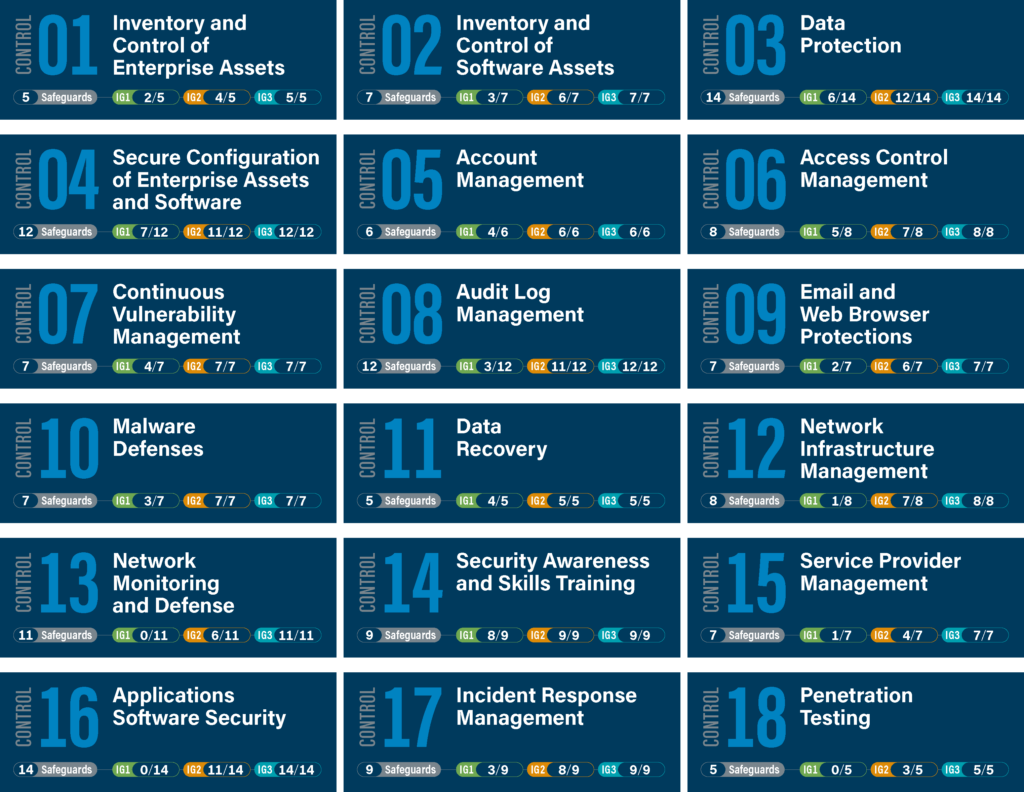
The CIS Controls, developed by the Center for Internet Security (CIS), is often considered an excellent starting point for small businesses or those without dedicated cybersecurity resources. This framework offers 18 prioritized security measures, including access management, data protection, and employee training. These controls are designed to provide maximum impact with minimal effort, making them ideal for SMBs with limited resources.
- A concrete example: A study conducted by CIS found that implementing the initial 20 controls helped reduce the risk of common cyberattacks by 85%.
- Key advantage: The framework is available for free download and includes ready-to-use checklists to help businesses get started quickly.
NIST Cybersecurity Framework: A Reference for Large Enterprises
Created by the National Institute of Standards and Technology (NIST), the NIST Cybersecurity Framework (CSF) is widely used by large enterprises and critical organizations. This framework focuses on five essential functions: Identify, Protect, Detect, Respond, and Recover.
Why choose NIST?: It offers unparalleled flexibility, allowing businesses to tailor the framework to their specific needs while complying with international regulatory requirements such as GDPR (Europe) or Law 25 (Quebec).
ISO 27001: The Certification for Government and Enterprise Trust
ISO 27001 is a globally recognized framework focused on information security management systems (ISMS). This standard is particularly suited for businesses looking to obtain certification to demonstrate their commitment to cybersecurity, especially those working with governments or within critical supply chains.
- Mandatory certification in some cases: An increasing number of Canadian government contracts require ISO 27001 compliance to ensure the security of their suppliers.
- Strengthening reputation: A study by BDO Canada highlights that ISO 27001 compliance helps businesses enhance their reputation and meet regulatory requirements, facilitating access to new markets and partnerships.
How to Choose the Right Framework for Your Business?
- Assess your needs: An SMB starting with cybersecurity may find CIS Controls sufficient, while a large enterprise with complex requirements may opt for NIST or ISO 27001.
- Define your objectives: Organizations seeking formal certification should prioritize ISO 27001, while those looking for a flexible framework might turn to NIST.
- Consider costs and resources: CIS Controls offer free access, whereas implementing NIST or ISO 27001 may require significant investment in time and expertise.
These frameworks are not just compliance tools; they also enable businesses to build a proactive cybersecurity posture, strengthening their resilience against current threats.
Risk Assessment: The Key to Effective Security
Risk assessment is a fundamental element of any cybersecurity strategy. According to Roland Winters, effective management begins with identifying and prioritizing threats, allowing SMBs to focus their efforts on the most critical areas.
Listing Potential Risks
To get started, it is essential to compile a comprehensive list of risks the company may face. These risks may include:
- Sensitive data theft: A data breach costs companies an average of $4.45 million, according to IBM’s 2023 Cost of a Data Breach Report.
- Regulatory non-compliance: With laws such as Law 25 in Quebec or GDPR in Europe, businesses face significant penalties for non-compliance. For instance, under Law 25, private companies risk fines of up to $25 million or 4% of their global annual revenue, whichever is higher.
- Financial impact of cyberattacks: In 2023, 60% of SMBs targeted by a cyberattack went bankrupt within six months, according to the Cyber Readiness Institute report.
Ranking Risks by Severity
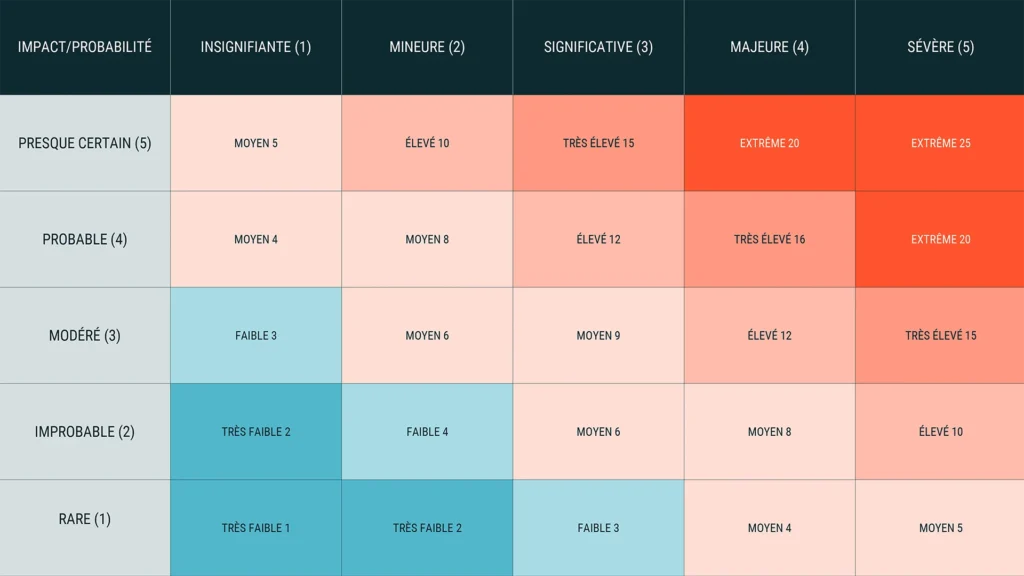
Once identified, risks should be prioritized based on their severity and likelihood of occurrence. Roland Winters recommends using a risk matrix, a visual tool that cross-references:
- Likelihood of occurrence: For example, targeted phishing has a high probability for SMBs with limited cybersecurity training.
- Potential impact: A ransomware attack that paralyzes operations can result in significant financial losses and reputational damage.
Risk matrices like these are widely used in organizations to guide strategic decision-making, as illustrated in the NIST Risk Management Guide.
Adopting a Maturity Model
To determine where a business stands on the cybersecurity scale, Winters recommends adopting a maturity model. This model measures the effectiveness of current practices and sets clear objectives for improvement:
- Level 0: Non-existent: No controls or established processes.
- Level 1: Ad hoc: Isolated efforts without a coherent strategy.
- Level 5: Optimized: An integrated approach with automated processes and continuous improvement.
Models such as the CMMI Cybermaturity Model help businesses assess themselves and prioritize investments. For example, an SMB at level 1 can aim for level 3 by improving access management and implementing regular employee training programs.
Why This Step Is Crucial
By assessing risks, SMBs can avoid unnecessary investments and focus their resources on the most relevant threats. This also enables them to meet the increasing security demands of clients and business partners.
Adopting a rigorous and progressive approach to risk assessment not only ensures data protection but also contributes to a company’s long-term sustainability in an increasingly hostile digital landscape.
Practical Solutions: Train, Equip, and Monitor
To effectively guard against cyber threats, it is crucial to build a robust cybersecurity strategy based on three fundamental pillars: people, processes, and technology. Roland Winters emphasized that cybersecurity is a continuous process requiring constant vigilance.
People: Training to Prevent Attacks
Employees represent the first line of defense against cyberattacks. However, according to a study by Proofpoint, 88% of data breaches in 2023 were caused by human errors. Training employees is therefore essential to reducing vulnerabilities.
- Phishing Awareness: Regular training sessions help employees recognize fraudulent emails and avoid clicking on malicious links, which can reduce phishing risks by 70%.
- Attack Simulations: Companies can conduct phishing tests to identify weaknesses and improve security behavior.
- Best Online Practices: Using strong passwords, enabling two-factor authentication, and securing both personal and professional devices.
Processes: Clear Policies to Structure Security
A well-defined cybersecurity policy sets guidelines for managing access, data, and incidents. Winters emphasized the importance of structuring these processes to prevent organizational vulnerabilities.
- Access Management: Restricting permissions to only those who need access to specific information, following the principle of least privilege.
- Incident Response Plan: A clear plan helps businesses react quickly in case of a breach, minimizing financial and reputational damage.
- Regular System Audits: Conducting periodic security assessments to identify and fix vulnerabilities before they can be exploited.
Technology: Investing Wisely
While technology is essential, it alone cannot guarantee complete cybersecurity. According to a Gartner survey, companies spend an average of 10% of their IT budget on cybersecurity, yet a significant portion of these investments is often poorly optimized.
- Advanced Protection Tools: Investing in solutions such as firewalls, intrusion detection systems (IDS), and next-generation antivirus software.
- Artificial Intelligence (AI) Solutions: Leveraging AI to automatically detect and counter threats in real time.
- Regular Backups: Maintaining offline data backups to prevent loss in case of a ransomware attack.
A Balanced and Continuous Approach
Roland Winters emphasized that a balanced approach—combining training, robust processes, and appropriate technologies—is the key to successful cybersecurity. He also highlighted that cybersecurity is never a final goal: threats constantly evolve, requiring regular updates to practices and tools.
For SMBs, the key lies in continuous vigilance and a long-term commitment to digital security. Businesses should view cybersecurity not as an expense but as a strategic investment ensuring their operational resilience.
Conclusion: Cybersecurity—A Constantly Evolving Strategic Imperative
Cybersecurity is not an expense but an essential strategic investment to ensure the longevity of SMBs in an ever-evolving digital world. Threats such as ransomware, phishing, and organized cybercrime are rapidly evolving, and their impact can be devastating—both financially and in terms of business reputation. Given these challenges, adopting a proactive approach is no longer an option but a necessity.
Following proven frameworks like CIS Controls or the NIST Framework enables businesses to structure their cybersecurity efforts while adapting to their level of maturity. However, protection is not limited to technology: training employees, integrating robust processes, and regularly assessing risks are essential actions to maintain a strong defensive posture.
Companies that invest in cybersecurity gain more than just protection against attacks. They also strengthen customer trust, comply with regulatory requirements such as Law 25 in Quebec, and increase their competitiveness—particularly when working with partners or governments that have high security standards.
By watching Roland Winters’ conference, you will not only gain insight into current challenges but also discover concrete solutions to secure your business. Take the time to act today—when it comes to cybersecurity, anticipating risks is always less costly than repairing the damage. Security is a continuous process, and every step taken brings your business closer to long-term digital resilience.

